ePact Achieves VMware Master Services Competency in Network Virtualization

Belgium, June 5, 2023 — ePact today announced that it has successfully achieved Network Virtualization VMware Master Services Competency. This competency demonstrates that ePact is committed to helping organizations accelerate their digital transformations by leveraging their validated services delivery capabilities around advanced VMware technologies.
ePact engages in new partnership with Tanium to provide converged endpoint management solutions to mid-market enterprises

November 24 2022 — ePact engages in new partnership with Tanium to provide converged endpoint management solutions to mid-market enterprises. %
Thanks to Trend Micro cure IT-security of UZ Brussel is up to speed again
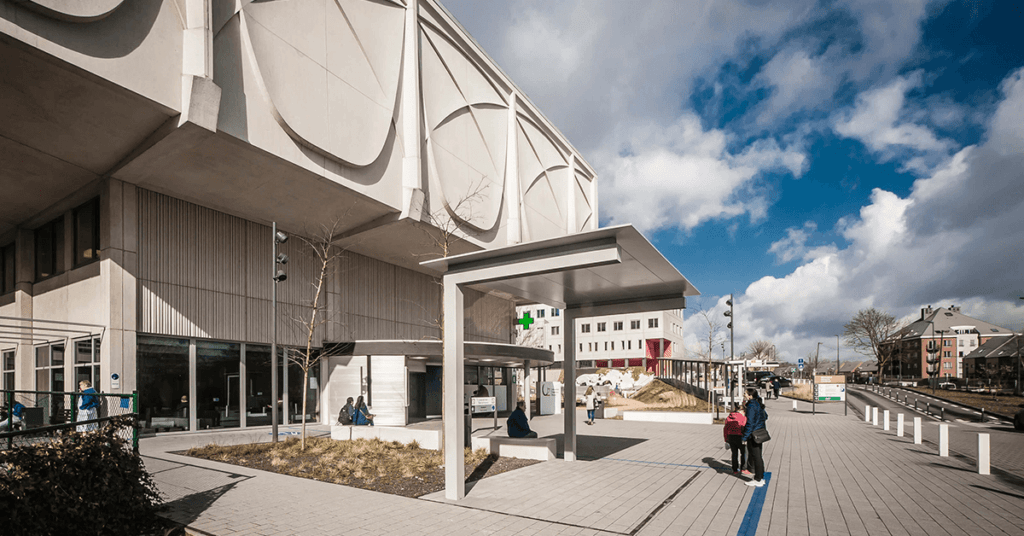
UZ Brussel University Hospital, located on the Jette campus, is one of the most important hospitals in Belgium with 721 beds. It was founded by the Vrije Universiteit Brussel (VUB) and several polyclinics at various locations on the outskirts of Brussels are attached to the hospital. These are also supported for various services – including IT – from UZ Brussel.
End of support for Windows Server 2008 and 2008 R2
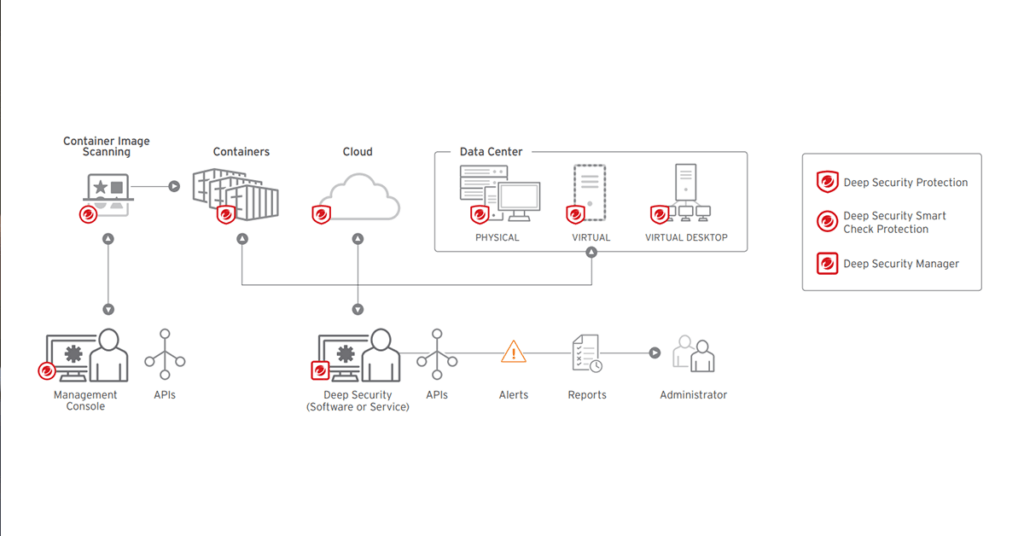
On January 14, 2020, Microsoft® will stop supporting Windows® Server 2008 and 2008 R2. This means that Microsoft will no longer provide security updates for new threats and vulnerabilities affecting these systems.
What skills do you need as an IT professional in 2020?

What skills do you need as an IT professional in 2020 Today, the skills of an ICT professional must go further than simply carrying out a well-defined set of tasks. Especially when you are in direct contact with customers, the communicative and empathic aspect becomes increasingly important. 1. Willing to learn If you have just […]
6 reasons why you should consider a cloud migration

6 reasons why you should consider a cloud migration to the cloud In 2020, the Cloud has become an indispensable part of the business world. We see that many companies have already made the step to the private, public or hybrid cloud and that this item is at the top of the agenda for others, […]
Cybersecurity awareness training for all employees

Cybersecurity awareness training for all employees Cyber attacks are becoming more common and hackers continue to develop new, innovative techniques. As a company, you probably invest a lot of resources to protect yourself against possible attacks. This is a good start, but it’s not everything Employees are your best defense or weakest link It may […]
5 safety tips for Black Friday shopping

5 safety tips for Black Friday shopping It’s that time of the year: Black Friday and Cyber Monday are almost here. On these days cybercriminals are on the hunt to steal your personal information and/or money. In this blog we therefore give you five tips to make bargains in an efficient and safe way without […]
6 data protection tips for employees

6 data protection tips for employees In a world where cyberattacks take place on a daily basis, data protection has never been more important. In this blog we give you an overview of some actions you can take to protect your personal or business information. 1. Watch out for phishing attacks Whoever has not heard […]
